Resource Management and Governance Overview
Overview
Resource Management in EmpowerID is a core capability that enables organizations to delegate day-to-day administration of digital assets—such as groups, users, roles, and applications—without compromising governance or security. It is distinct from processing and configuration management, which involves the design and operation of the policies and workflows that govern system behavior.
EmpowerID separates these concerns to support different personas within the organization. Processing and configuration management is typically the domain of trained system administrators and IAM professionals. These individuals are responsible for managing EmpowerID’s underlying business processes, workflows, and policy settings—essentially shaping how the platform behaves and responds to changes in the environment.
In contrast, resource management focuses on the operational oversight of individual objects within the system. This includes managing the lifecycle, ownership, access policies, and visibility of users, groups, computers, management roles, applications, shared credentials, and other protected resources. Crucially, EmpowerID allows this form of management to be delegated to individuals who may not have deep technical expertise, but who have business responsibility for the resources in question. These delegated users typically interact with the system through simplified interfaces and guided workflows.
To support this model, EmpowerID provides two different management interfaces:
-
Resource Admin Interface: A streamlined microservice designed for non-technical or semi-technical users. It provides an intuitive and guided experience for managing resources using workflows and user-friendly pages. This is the interface most often used by distributed owners or responsible parties.
-
Classic Admin Interface: A more detailed, technical interface intended for system administrators. It offers full control over the configuration of resources and policies through a tabbed interface with access to advanced search, metadata editing, and policy assignment features.
At the heart of EmpowerID’s resource management model is the concept of ownership—both in terms of business responsibility and access control. The system supports two distinct ownership models: the Responsible Party (or Owner Assignee ID), which is a single user accountable for the resource’s lifecycle, and the RBAC Owner (or Access Manager), which is a multi-user assignment that governs access permissions through EmpowerID’s RBAC engine. These ownership models are used throughout the platform to delegate access, drive approval workflows, and support recertification processes.
By distributing responsibility through clearly defined ownership roles and providing tailored interfaces for different types of users, EmpowerID empowers organizations to maintain security and compliance while reducing the operational burden on central IT.
Understanding EmpowerID Interfaces for Resource Management
EmpowerID provides two distinct interfaces for managing resources, each designed to meet the needs of different types of users: the Resource Admin Interface and the Classic Admin Interface. These interfaces are intentionally structured to separate administrative complexity from delegated resource ownership, ensuring that both technical and non-technical users can effectively manage the assets under their purview.
Resource Admin Interface
The Resource Admin interface is part of EmpowerID’s microservices architecture and serves as the primary tool for non-technical or semi-technical users who are responsible for managing specific resources. These users might include business unit leaders, application owners, or group managers who need to maintain their resources without needing deep familiarity with IAM systems or configuration settings.
Designed for simplicity and ease of use, this interface presents information in a user-friendly format and leverages guided workflows that walk users through resource management tasks step by step. It abstracts away technical complexity and allows users to focus on the responsibilities relevant to their roles—such as updating ownership, adjusting group membership, or initiating specific workflows.
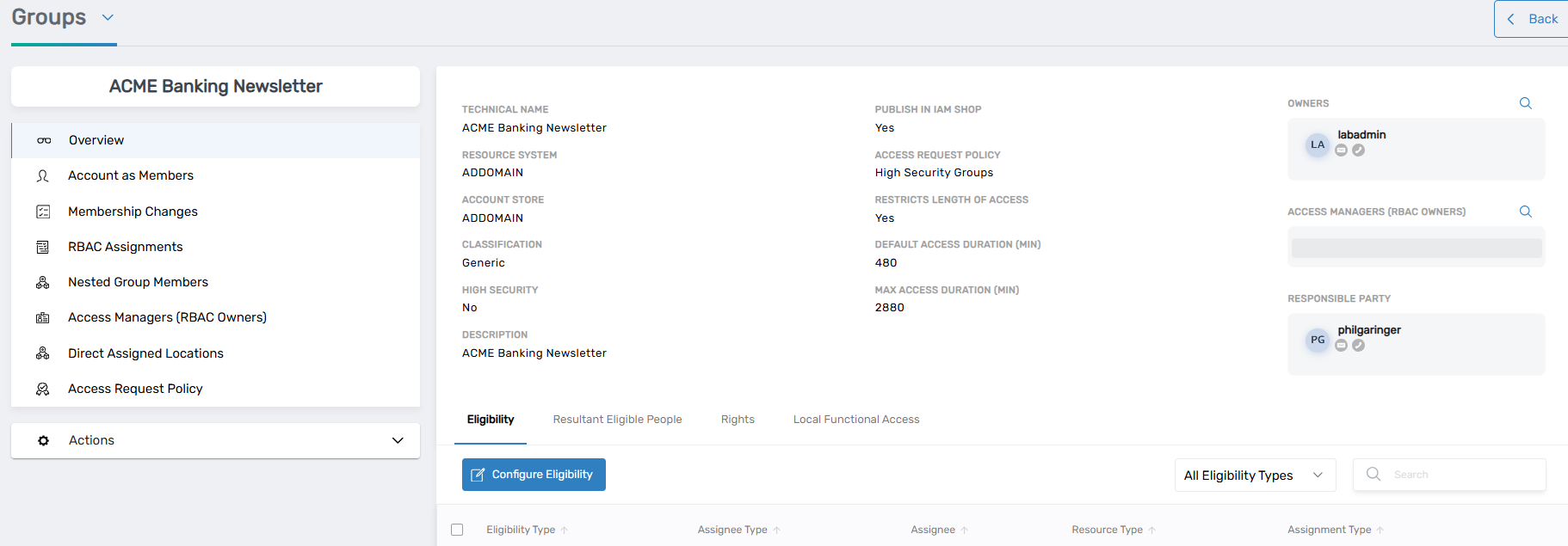
Users interact with a filtered view of resources, often defaulting to resources for which they are the designated owner or responsible party. This makes it easier for individuals to quickly identify and manage the assets they oversee. When managing a specific resource—such as a group—users can access a Details page that presents high-level information like publication to the IAM Shop, current access policies, and assigned owners. The screen also typically includes controls to configure eligibility or visibility rules and provides access to action menus, such as launching the Manage Wizard.
The Manage Wizard itself is a powerful component of the Resource Admin interface. It guides users through common operations—such as modifying metadata, adjusting ownership, or reviewing group members—via a series of intuitive, step-by-step workflow pages. If a resource is already selected when launching the wizard, the workflow bypasses the selection stage entirely, streamlining the process even further.
Ultimately, the Resource Admin interface empowers business-aligned users to maintain control over the digital resources they own, while still participating in the governance and auditing workflows enforced by EmpowerID.
Classic Admin Interface
In contrast, the Classic Admin interface is designed for technical administrators who require a more robust and comprehensive management experience. This interface exposes the full range of settings and metadata for each resource type and includes advanced features for policy management, attribute editing, and auditing.
Navigation in the Classic Admin interface is centered around resource types—such as groups or management roles—with each type presenting a list of available resources. The search capabilities in this interface are considerably more powerful than in the Resource Admin interface, allowing technical users to perform complex queries. For example, administrators can filter groups by attributes such as membership, mail enablement, system type, or specific attribute values.
Once a resource is selected, users are presented with a View One page that includes general information such as responsible party, access managers, direct location assignments, and published policies. This view also allows direct editing of many key properties right from the overview tab, making it highly efficient for users who know exactly what they want to update.
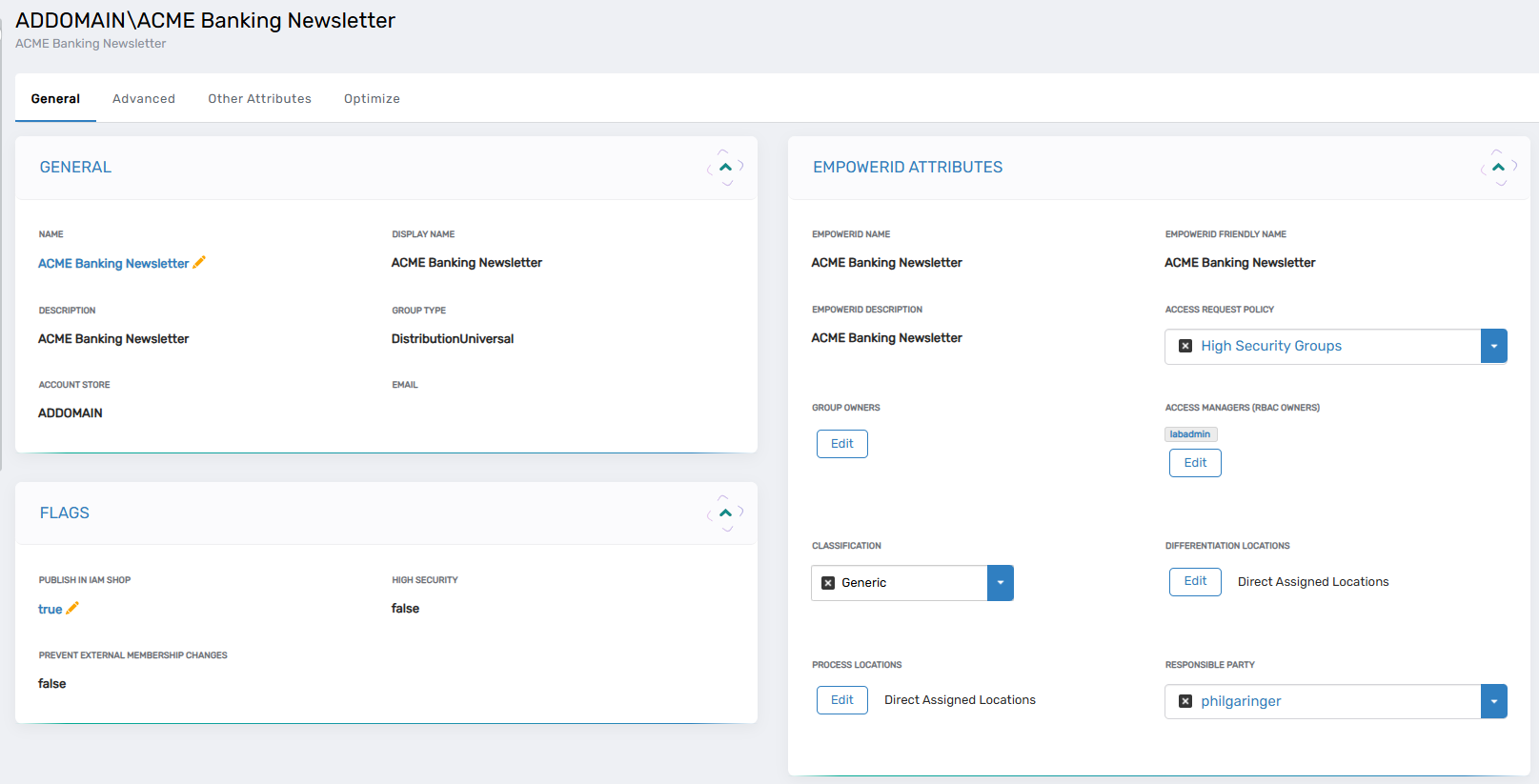
Beyond the general tab, the Classic Admin interface offers additional tabs such as Advanced, Access, and Attributes, each of which exposes more granular data. The Advanced tab includes membership data such as attribute-based membership rules, pre-approved just-in-time members, and resultant membership calculations. The Access tab displays PBAC and RBAC policy associations and access rule sets. The Attributes tab reveals standard and extension attributes, offering a complete view into the resource’s metadata.
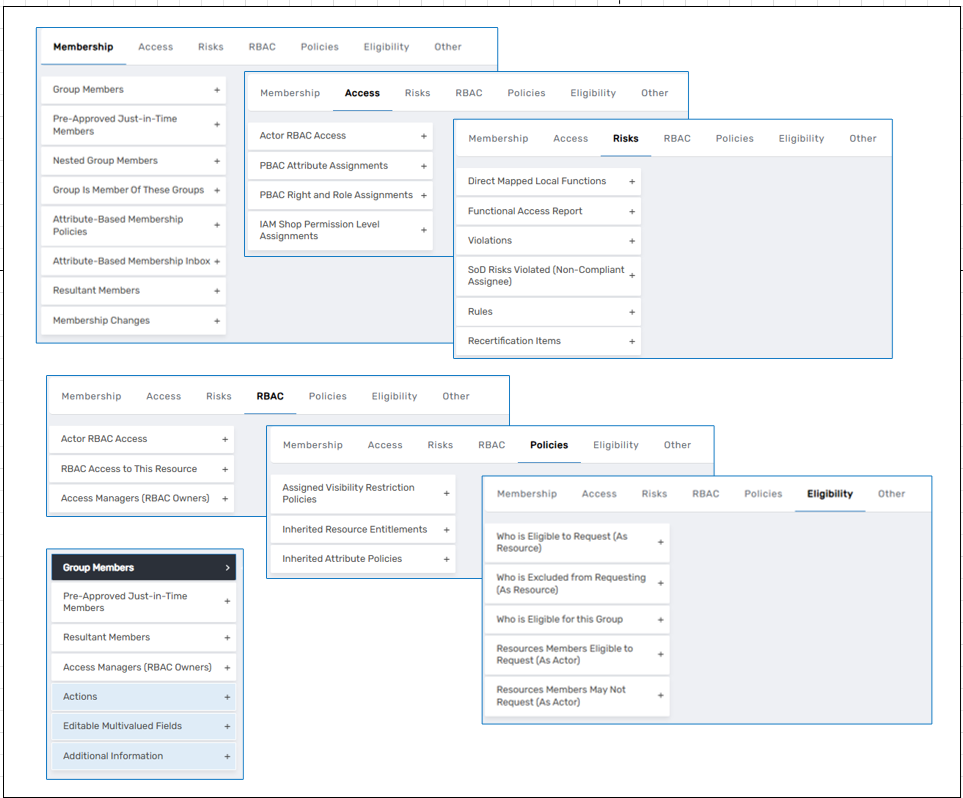
A notable feature of the Classic Admin interface is the Edit One page. This unified editor enables users to update nearly all aspects of a resource from a single location. In addition to standard fields like name and description, administrators can configure locale keys, system flags (such as “prevent deletion”), and custom notes.
It's important to note that workflows initiated from the Classic Admin interface are often different from those triggered in the Resource Admin interface. Because the Classic Admin interface is designed for system administrators, some actions—such as changing ownership or policy associations—may not require approval and may bypass the standard approval flow entirely. This streamlines administrative tasks but also highlights the need for role-based access controls to ensure that only authorized users have access to this interface.
Core Concepts in Resource Ownership
Ownership plays a foundational role in EmpowerID’s approach to delegated administration and access control. EmpowerID distinguishes between two types of ownership models that apply to nearly all resource types: the Responsible Party (also referred to as the Owner Assignee ID) and the RBAC Owner (also known as the Access Manager). These two designations serve different—but often complementary—purposes in both governance and access delegation.
Responsible Party (Owner Assignee ID)
The Responsible Party is a single person object assigned to a resource to represent the individual with ultimate business accountability for that resource. This role is not about technical administration but about operational oversight. Responsible Parties are typically designated for critical resources such as user accounts, groups, management roles, applications, computers, shared credentials, and locations.
This ownership designation is used extensively in EmpowerID for processes such as:
- Recertification: Responsible Parties are the primary approvers in recertification tasks related to the resources they oversee. They receive tasks prompting them to confirm whether the resource is still needed or whether its assignments are still valid.
- Resource Lifecycle: These individuals make decisions about whether a resource should be retained, renamed, modified, or deleted. They are considered the authoritative owner from a business perspective.
The Responsible Party is also a key identity in audit records, ensuring traceability for administrative decisions and lifecycle actions related to the resource.
EmpowerID allows organizations to easily transfer this responsibility in the event of personnel changes. This can be done manually, through the Transfer Responsibilities workflow, or automatically as part of a planned leaver event using EmpowerID’s no-code automation. This ensures continuity in governance and avoids the risk of orphaned resources—objects that no longer have an assigned responsible party. Built-in reports help identify these orphaned resources to allow remediation.
Importantly, the Responsible Party relationship is always one-to-one: each resource has exactly one Responsible Party at any given time.
RBAC Owner (Access Manager)
In contrast to the singular Responsible Party model, the RBAC Owner—or Access Manager—is a multi-valued access level assigned through EmpowerID’s Role-Based Access Control (RBAC) framework. Every resource in EmpowerID can have one or more RBAC Owners, and these assignments are used to denote individuals who are authorized to manage or interact with the resource at a permission level defined by their role.
The Access Manager designation is a pre-compiled RBAC access level that is optimized for fast, consistent access control decisions. In many EmpowerID interfaces, the “owners” listed for a resource are determined dynamically by querying which users have the Access Manager level for that specific resource.
This model supports dynamic delegation. For instance, you can assign visibility or permissions to someone based on a relative assignment such as: “give access to all resources for which the person is an Access Manager” or “delegate administrative permissions to those who are Responsible Party for a given set of groups.”
RBAC Owners are often used in:
- Delegation Scenarios: Where multiple users should have administrative rights over a resource.
- Access Control: To determine who can view, edit, or manage a resource through RBAC policies.
- Interface Filtering: So that users only see the resources for which they have relevant authority.
Combining Ownership Models
While the Responsible Party and Access Manager serve distinct purposes, many organizations choose to consolidate them for operational simplicity. A common pattern is to automatically assign the Access Manager role to any user who is designated as the Responsible Party for a given resource. This effectively allows the same individual to serve both as the authoritative business owner and the functional access administrator.
This hybrid model ensures that the person responsible for a resource also has the technical means to manage it—eliminating the need for additional delegation unless otherwise required. It also simplifies policy design, allowing RBAC and approval workflows to reference either ownership model as needed.
EmpowerID supports this flexibility through relative assignment types, enabling policy designers to grant access based on statements like “is the Responsible Party of the resource” or “is an RBAC Owner of the resource.” These constructs are especially useful when defining visibility scopes, delegation rights, and access review responsibilities across the system.
In short, resource ownership in EmpowerID is not just a descriptive field—it is an integral part of the platform’s identity governance model, driving visibility, access, delegation, and policy enforcement in a scalable and auditable way.